Direct Send Phishing: Threats to Financial Institutions
Explore the rising threat of direct send phishing attacks targeting financial institutions. Learn how these attacks exploit Microsoft 365 vulnerabilities, and discover effective mitigation strategi...
Saiprashanth Pulisetti
7/28/20258 min read
As cybercriminals continue to evolve their tactics, financial institutions face an unprecedented wave of sophisticated phishing attacks that bypass traditional security measures. Among these emerging threats, the Direct Send method represents a particularly insidious technique that exploits legitimate Microsoft 365 features to launch convincing spear-phishing campaigns. For Security Operations Center (SOC) teams tasked with defending financial organizations, understanding this threat landscape has never been more critical.
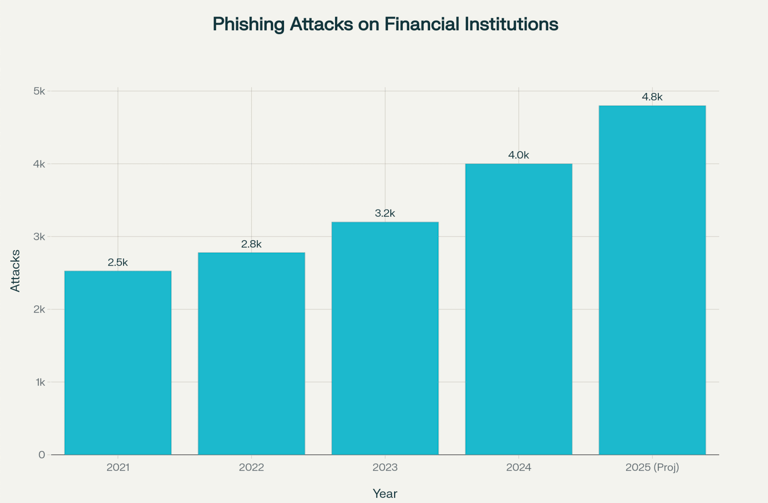
Recent data reveals that financial services organizations experienced a 25% increase in advanced email attacks in 2024, with phishing attacks specifically targeting the sector rising by 17%. With over 3.4 billion phishing emails sent daily globally, and financial institutions receiving approximately 1,990 phishing attempts per 1,000 employees annually, the stakes have never been higher.
Understanding the Direct Send Phishing Method
What is Direct Send?
The Direct Send method represents a significant evolution in phishing tactics, specifically targeting organizations using Microsoft 365 Exchange Online. This technique exploits Microsoft 365's Direct Send feature, which was originally designed to allow internal devices like printers and scanners to send emails without authentication[3]. The feature utilizes smart hosts with predictable formats (e.g., tenantname.mail.protection.outlook.com) and requires no credentials, tokens, or access to the tenant[3].
How Direct Send Phishing Works
Cybercriminals have weaponized this legitimate functionality to conduct sophisticated phishing campaigns that appear to originate from within the target organization. The attack methodology follows these steps:
Target Identification: Attackers identify vulnerable organizations by examining their MX records and email infrastructure
Domain Spoofing: Using publicly available information, they craft emails that appear to come from internal users
Message Delivery: Emails are sent through Microsoft's infrastructure, bypassing many traditional security controls
Trust Exploitation: Recipients receive messages that appear to be from trusted internal colleagues, increasing the likelihood of successful deception
According to Varonis research, this campaign has targeted over 70 organizations across multiple industries since May 2025, with threat actors using PowerShell to automate email delivery through smart hosts[3][4]. The spoofed emails often masquerade as internal communications such as voicemail notifications, containing malicious PDFs with QR codes designed to steal credentials[5].
The Evolution of Phishing Threats Against Financial Institutions
Historical Context
Phishing attacks have plagued the financial sector for decades, but their sophistication has increased dramatically. The sector has experienced some of the most costly phishing incidents in history, including the Facebook and Google attack that resulted in $100 million in losses between 2013 and 2015[6], and the Crelan Bank incident that cost €75.8 million.
Financial institutions remain prime targets because they:
Handle massive volumes of sensitive data
Process billions in daily transactions
Maintain extensive networks of high-net-worth clients
Operate under strict regulatory compliance requirements
Current Threat Landscape
The modern phishing landscape targeting financial institutions is characterized by several alarming trends:
AI-Enhanced Attacks: Generative AI tools now enable cybercriminals to create highly personalized, context-appropriate phishing emails at scale. Research indicates that 73.8% of all phishing emails analyzed in 2024 exhibited some use of AI, increasing to 90.9% for emails with polymorphic elements.
Polymorphic Campaigns: These sophisticated attacks consist of nearly identical emails that differ only by small details, making them extremely difficult for traditional security systems to detect. 76.4% of all phishing attacks in 2024 contained at least one polymorphic feature.
Ransomware Integration: The period from September 2024 to February 2025 saw a 22.6% increase in ransomware payloads delivered through phishing emails, with the trend accelerating to a 57.5% increase in the final months of 2024.
Business Email Compromise: The $26 Billion Threat
Business Email Compromise (BEC) attacks represent a particularly devastating threat to financial institutions. These sophisticated schemes involve attackers gaining access to corporate email accounts and impersonating executives to authorize fraudulent transactions. 64% of financial institutions reported experiencing BEC attacks in 2024, with average losses of $150,000 per incident.
Notable BEC cases affecting financial institutions include:
FACC: Lost €42 million when an employee transferred funds based on a fake CEO email
Crelan Bank: Suffered €75.6 million in losses through executive impersonation
Recent Indian Case: Infrastructure company MEIL lost ₹5.5 crore ($660,000) when attackers impersonated a Dutch vendor's representative
Technical Analysis of Direct Send Vulnerabilities
Infrastructure Requirements
The Direct Send vulnerability affects organizations that:
Use Microsoft 365 Exchange Online services
Have predictable MX record formats (company.mail.protection.outlook.com)
Rely on external mail proxy providers like Mimecast
Have not implemented specific connector restrictions
Attack Indicators
SOC teams should monitor for the following indicators of Direct Send abuse:
Anomalous Geolocation: Emails originating from unexpected IP addresses, particularly foreign locations
PowerShell User Agents: Email activity showing PowerShell as the user agent without corresponding authentication events
Self-Addressed Emails: Users receiving emails from their own addresses without legitimate business justification
QR Code Attachments: PDFs containing QR codes directing to credential harvesting pages.
Detection Challenges
Direct Send attacks present unique detection challenges:
Messages route through legitimate Microsoft infrastructure
No authentication failures generate alerts
Traditional email security gateways may not flag internal-appearing emails
Trust relationships within organizations reduce user suspicion.
Comprehensive Mitigation Strategies
Immediate Technical Controls
1. Enable Reject Direct Send
Organizations should immediately enable the 'Reject Direct Send' option in the Exchange Admin Center. This blocks unauthenticated emails appearing to originate from internal domains. The setting should be combined with strict DMARC p=reject policies and SPF hard-fail configurations[5][11].
2. Implement Connector Restrictions
Configure Exchange Admin Center connector rules to force all incoming mail through trusted mail gateways. Mail should not be allowed into the organization from untrusted sources. Specific IP address restrictions should be enforced in SPF records.
3. Advanced Email Filtering
Deploy AI-powered email security solutions that can:
Analyze sender behavior patterns
Detect anomalous internal communications
Identify suspicious attachments and links
Implement real-time threat intelligence feeds.
Organizational Security Measures
Multi-Factor Authentication (MFA)
Implement mandatory MFA across all email accounts and critical systems. Financial institutions should use a combination of:
Password-based authentication
Security tokens or mobile app authenticators
Biometric verification for high-privilege accounts.
Zero Trust Architecture
Adopt a zero-trust approach that:
Verifies every user and device
Implements least-privilege access principles
Continuously monitors and validates security posture
Requires authentication for all internal communications.
Employee Training and Awareness
Establish comprehensive security awareness programs featuring:
Regular phishing simulation exercises
Industry-specific threat briefings
Clear reporting procedures for suspicious emails
Incentive programs for security-conscious behavior.
SOC Response Framework for Phishing Incidents
Detection and Analysis Phase
When phishing incidents are detected, SOC teams should follow a structured approach:
Initial Triage
Review user reports and gather relevant information
Assess potential impact and severity levels
Document incident details including timestamps and affected users
Classify the incident type (BEC, credential phishing, malware delivery).
Email Analysis
Examine email headers using forensic tools
Analyze sender reputation through threat intelligence platforms
Inspect URLs and attachments in isolated environments
Extract and catalog indicators of compromise (IOCs).
Containment and Response
Immediate Actions
Reset credentials for affected users
Block malicious domains and IP addresses
Quarantine suspicious emails across the organization
Implement network segmentation if necessar.
Communication Strategy
Notify relevant stakeholders including executive leadership
Issue security alerts to all employees
Report incidents to regulatory bodies as required
Coordinate with law enforcement for criminal investigations.
Recovery and Lessons Learned
System Restoration
Remove malicious content from affected systems
Verify the integrity of critical data and systems
Implement additional monitoring for affected accounts
Conduct thorough security assessments.
Post-Incident Analysis
Document attack vectors and defensive gaps
Update security policies and procedures
Enhance employee training based on lessons learned
Share threat intelligence with industry partners.
Regulatory Compliance and Framework Alignment
Key Regulatory Requirements
Financial institutions must align their phishing defense strategies with relevant regulatory frameworks:
FFIEC Cybersecurity Assessment Tool (CAT)
The Federal Financial Institutions Examination Council provides comprehensive guidance for cybersecurity risk assessment, emphasizing the need for:
Robust email security controls
Incident response capabilities
Continuous monitoring programs
Regular security awareness training.
NIST Cybersecurity Framework
The framework's five core functions—Identify, Protect, Detect, Respond, and Recover—provide a structured approach to phishing defense:
Identify: Asset management and risk assessment
Protect: Access controls and security awareness training
Detect: Security monitoring and anomaly detection
Respond: Incident response planning and communication
Recover: Recovery planning and continuous improvement
DORA and NIS2 Compliance
European financial institutions must address Digital Operational Resilience Act (DORA) and NIS2 Directive requirements by implementing:
Encryption for sensitive communications
Recipient authentication mechanisms
Secure email delivery protocols
Data loss prevention configurations
Advanced Security Technologies and Solutions
AI-Powered Email Security
Modern email security solutions leverage artificial intelligence to:
Analyze communication patterns and detect anomalies
Identify polymorphic phishing campaigns
Provide real-time threat intelligence
Automate incident response workflows
Key Features to Evaluate:
Behavioral analytics capabilities
Integration with existing security infrastructure
Compliance reporting and audit trails
Scalability for enterprise environments
S/MIME and Email Encryption
Financial institutions should implement S/MIME (Secure/Multipurpose Internet Mail Extensions) certificates to
Digitally sign outbound emails
Encrypt sensitive communications
Verify sender authenticity
Prevent email tampering
Verified Mark Certificates (VMCs)
VMCs provide visual authentication of legitimate emails by displaying organizational logos directly in email clients, helping users identify authentic communications from their financial institutions.
Industry Collaboration and Threat Intelligence
FS-ISAC Partnership
The Financial Services Information Sharing and Analysis Center (FS-ISAC) provides critical threat intelligence and incident response support. The organization's "Stop the Scams" framework offers four essential actions:
Collect and Share Intelligence: Gather actionable intelligence from consumers and disseminate across relevant departments
Educate Employees and Customers: Develop awareness programs highlighting phishing tactics
Catalog Communication Channels: Maintain directories of legitimate contact methods to prevent spoofing
Leverage Anti-Phishing Technologies: Implement advanced detection and prevention solutions
Threat Intelligence Integration
SOC teams should integrate multiple threat intelligence sources:
Commercial threat feeds
Open source intelligence (OSINT)
Industry-specific indicators
Government security advisories
Peer organization intelligence sharing
Emerging Threats and Future Considerations
QR Code Phishing (Quishing)
A concerning trend involves the use of QR codes in phishing attacks, particularly those targeting Microsoft Teams users. These attacks involve:
Fake Microsoft tenants and deceptive domains
QR codes embedded in PDF attachments
Adversary-in-the-middle (AiTM) techniques to bypass MFA
Mobile-first attack vectors exploiting device trust
Deepfake and Voice Cloning
Advanced AI technologies enable attackers to create convincing deepfake videos and voice clones of executives, adding new dimensions to social engineering attacks. Financial institutions must prepare for:
Multi-channel verification procedures
Enhanced voice authentication systems
Employee training on emerging deception techniques[25]
Building Organizational Resilience
Incident Response Testing
Regular testing of incident response procedures through:
Tabletop exercises simulating phishing scenarios
Red team assessments of email security controls
Crisis communication drills
Recovery time objective (RTO) validation
Continuous Improvement Processes
Establish feedback loops that:
Analyze attack trends and defensive effectiveness
Update security policies based on emerging threats
Enhance employee training programs
Optimize security technology configurations
Executive Leadership Engagement
Ensure C-suite commitment through:
Regular cybersecurity briefings and risk assessments
Board-level oversight of security investments
Clear accountability structures for security outcomes
Integration of security metrics into business performance indicators.
Conclusion: A Multi-Layered Defense Strategy
The Direct Send phishing method represents just one facet of an evolving threat landscape that specifically targets financial institutions' trust relationships and operational dependencies. As cybercriminals continue to exploit legitimate technologies and human psychology, financial organizations must adopt comprehensive, multi-layered defense strategies that combine advanced technical controls with robust organizational processes.
The key to effective defense lies in understanding that no single solution can address the full spectrum of phishing threats. Instead, financial institutions must implement integrated approaches that encompass:
Technical Excellence: Deploy AI-powered email security solutions, implement strict authentication protocols, and maintain comprehensive monitoring capabilities
Human-Centric Security: Invest in continuous employee education, establish clear reporting procedures, and foster security-conscious organizational cultures
Operational Resilience: Develop robust incident response capabilities, maintain regulatory compliance, and ensure rapid recovery from security incidents
Industry Collaboration: Participate in threat intelligence sharing, leverage security frameworks, and learn from peer organization experiences
For SOC teams defending financial institutions, the Direct Send threat underscores the importance of staying ahead of attacker innovation. By understanding these evolving techniques, implementing comprehensive mitigation strategies, and maintaining vigilant monitoring postures, security professionals can help protect their organizations against the most sophisticated phishing campaigns.
The financial sector's critical role in global economic stability demands nothing less than the highest standards of cybersecurity excellence. As the threat landscape continues to evolve, so too must our defensive capabilities, ensuring that trust in financial institutions remains well-founded and that customer assets remain secure in an increasingly digital world.
This blog post is based on current threat intelligence and best practices as of 2025. Organizations should consult with cybersecurity professionals and stay updated with the latest threat intelligence from trusted sources like FS-ISAC, NIST, and other industry authorities.
Sources:
https://mitigata.com/blog/types-of-phishing-emails/
https://bfore.ai/blog/what-is-a-spoofing-attack-what-financial-institutions-need-to-know/
https://attack.mitre.org/techniques/T1566/
https://www.getastra.com/blog/security-audit/phishing-attack-statistics/
https://adlumin.com/post/what-is-a-spoofing-attack-how-financial-institutions-are-being-targeted/
https://arcticwolf.com/resources/glossary/phishing/
https://abnormal.ai/blog/financial-services-email-attack-trends
https://hoxhunt.com/guide/phishing-trends-report
https://www.cisco.com/site/us/en/learn/topics/security/what-is-phishing.html
https://www.open-systems.com/blog/critical-role-email-security-financial-services-bifs/
https://www.techmagic.co/blog/blog-phishing-attack-statistics
https://blog.barracuda.com/2023/07/03/banks-have-lost-millions-to-these-common-attacks
https://www.bluevoyant.com/knowledge-center/8-phishing-types-and-how-to-prevent-them
https://aag-it.com/the-latest-phishing-statistics/
https://register.bank/insights/phishing-overview-banking/
https://www.checkpoint.com/cyber-hub/threat-prevention/what-is-phishing/8-phishing-techniques/
https://www.upguard.com/blog/biggest-cyber-threats-for-financial-services
https://www.varonis.com/blog/direct-send-exploit
https://www.knowbe4.com/hubfs/Phishing-Threat-Trends-2025_Report.pdf
https://www.mindpointgroup.com/blog/what-are-the-top-5-threats-a-soc-can-detect
https://petri.com/microsoft-365-direct-send-steal-credentials/
https://www.cloudflare.com/learning/access-management/phishing-attack/
https://cwsisecurity.com/a-guide-to-phishing-attacks-in-2025/
https://swimlane.com/blog/mobile-phishing/
https://arcticwolf.com/resources/blog/arctic-wolf-observes-microsoft-direct-send-abuse/
https://www.jumpsec.com/guides/microsoft-direct-send-phishing-abuse-primitive/
https://www.trendmicro.com/en_in/what-is/phishing/types-of-phishing.html
https://radiantsecurity.ai/learn/phishing-and-bec-attack-prevention/
https://success.culture.ai/knowledge/setting-up-direct-send-for-simulated-phishing-emails
https://s29837.pcdn.co/trendsreports/
https://www.eye.security/blog/microsoft-teams-chat-the-rising-phishing-threat-and-how-to-stop-it
https://safesendsoftware.com/secure-email-tips-for-financial-organizations/